File Integrity Monitoring Software




 (1 votes, average: 5.00 out of 5)
(1 votes, average: 5.00 out of 5)File Integrity Monitoring (FIM) alerts you to changes in critical system files, configuration files, and content files. Xcitium Advanced Endpoint Protection (AEP) combines FIM with other essential security capabilities to meet compliance requirements and get complete security visibility in a single, easy-to-use solution.
- Home
- Endpoint Protection
- File Integrity Monitoring
Change can be good.
File Integrity Monitoring: But not for a security professional.
Changes on critical servers can signal a breach. For that reason, it’s critical to use File Integrity Monitoring (FIM) for your critical servers so you’re alerted as changes happen. In fact, if those servers are in-scope for compliance, PCI DSS requirements 10.5.5 and 11.5 state you must install file integrity monitoring software in order to pass your audit.
With Xcitium, you have continual assurance of the integrity of security configurations along with complete visibility and control of all change for your continuous monitoring, change audit and compliance demands. FIM tracks who has accessed sensitive data on in-scope systems as well as what they did to that data. This audit trail allows you to validate that the changes were authorized, expected, and did not jeopardize the integrity and security of the data.
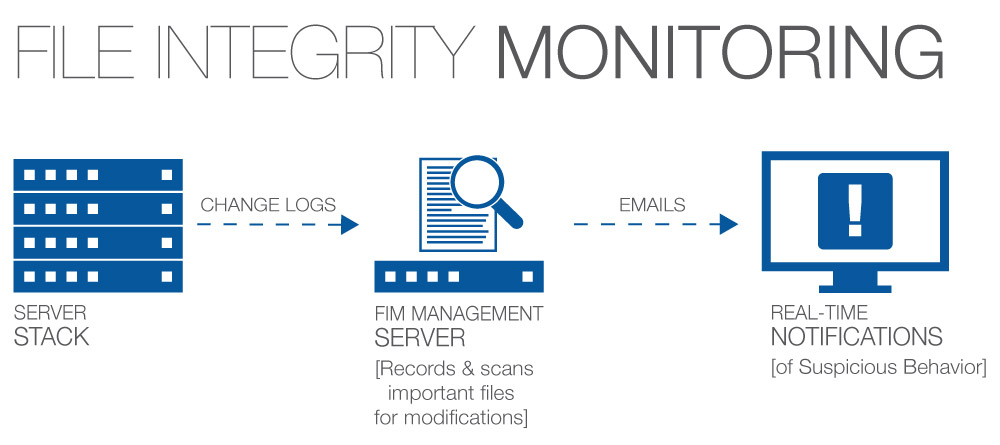
File Integrity Monitoring: Features and Benefits
- Create Focus – Xcitium Advanced Endpoint Protection provides the unique capability that helps IT Security teams focus on changes that matter. Save time and resources with a solution that is intuitive and responsive.
- Real–Time Intelligence – Get real–time detection of change‚ anomalies and threat indicators that enable you to address trouble spots quickly. Xcitium AEP delivers the intelligence you need quickly‚ so you can limit damage.
- Deeper Insights – Xcitium’s agent–based deployment provides deeper insight into system security configuration and change. This information reduces the guesswork from what happened‚ when and by whom. Obtain results you can depend on.
- Integration – We deliver a complete system including change ticketing integration. Save time by automating the compromise of detected changes and validate that the planned changes have really occurred.