Endpoint Detection: How What We Do For Detection?




 (1 votes, average: 5.00 out of 5)
(1 votes, average: 5.00 out of 5)Xcitium utilizes a wide variety of techniques to detect and identify unknown files, ranging from a basic signature-based system to emulators and from machine-learning techniques to reputation-based analysis. This holistic approach gives both detection of and protection from malware.
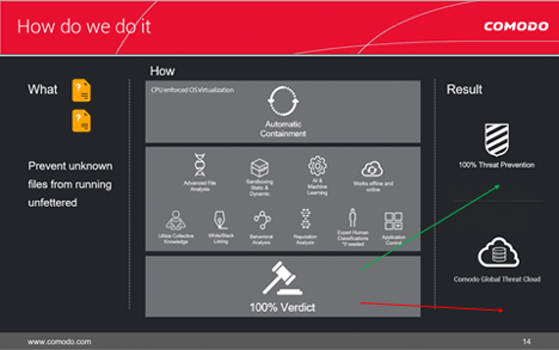
Our Default deny approach is the main defense mechanism for protection implemented as a unique containment [OS Virtualization] technology on the endpoint that provides both isolation of potential damage from malware and also usability due to the extensive whitelisting capabilities of our systems. For detection, static, dynamic and reputation-based systems are successfully blended to create a powerful engine that can detect zero-day malware that no other engine is able to identify. The cloud-based file analysis system enables the detection of almost all malware instantly. Additionally, expert human analysis may also be performed for detection, a unique feature that guarantees 100 percent detection for all malware files.
The following capabilities explain how we detect known malware and prevent infection from unknown (zero day) threats at the endpoint and in the cloud. They comprise the multiple layers of detection in Xcitium® Advanced Endpoint Protection.
Xcitium is the only security vendor with a Default Deny platform that allows full usability of unknown files while they run in Secure Auto Containment™ until automatic and expert human analysis delivers a trust verdict of good or bad. Xcitium Advanced Endpoint Protection allows the good applications, blocks the bad and contains the unknown files to prevent the damage from unknown malware. Only good files run unfettered on your endpoints.
What We Do For Detection: Zero Infection,
Zero damage.
What we do to detect known malware and prevent infection from unknown (e.g. zero day) threats.
Related Sources: