Holistic Approach to Endpoint Security
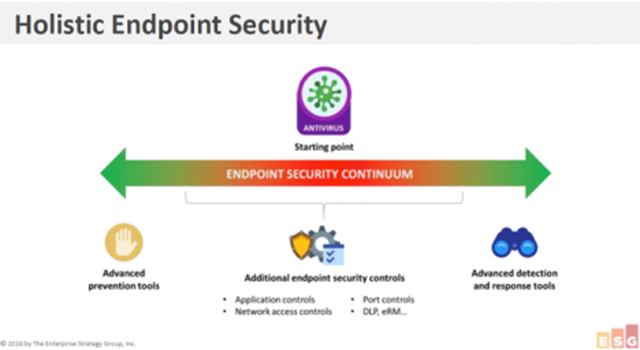
Comodo takes a holistic approach to endpoint security similar to what ESG refers to as the Endpoint Security Continuum. Our holistic approach spans simple signature-based detection of known malware to application whitelisting to advanced detection and response tools at the local level and in the cloud. Comodo’s endpoint security continuum also includes application and network access controls, a host intrusion prevention firewall (HIPS) and patent-pending Secure Auto Containment™ for usability while preventing infection from unknown malware.
Default Deny Platform Maximizes Security and Usability
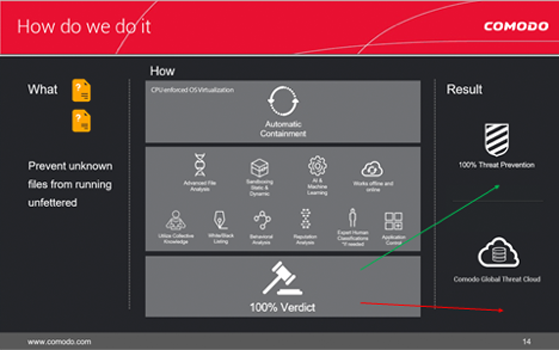
Unlike conventional and automated next-generation security solutions that rely on detection, Comodo Advanced Endpoint Protection combines extensive detection methods with continuous monitoring and secure auto containment to prevent the damage from unknown (zero day) malware.
Comodo is the only security vendor with a Default Deny Platform that allows full usability of unknown files while they run in Secure Auto Containment™. Automatic static and dynamic analysis of unknown files, and if needed, manual expert human analysis deliver a trust verdict of good or bad on every file.
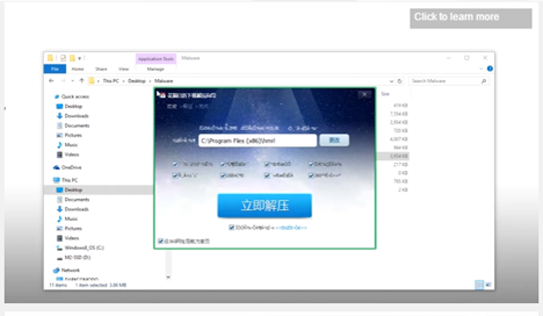
Watch how it works in this Advanced Endpoint Protection demo video.
With game changing Default Deny security and usability combined with comprehensive device control and endpoint management, enterprises can lower operational costs and prevent the damage from malware.
What We Do for Advanced Endpoint Protection
While the Comodo Global Threat Cloud continuously updates threat intelligence to protect the many enterprise threat vectors from attack, the Comodo ONE IT operating platform integrates IT and security management across the enterprise, providing visibility and control from a single pane of glass.
At the endpoint, Advanced Endpoint Protection combines a broad spectrum of Endpoint Protection Platform (EPP) and Endpoint Detection and Response (EDR) capabilities to block known malware and prevent infection from unknown threats.